INTRUSION PREVENTION
Attackers are increasingly turning to highly targeted external and internal attacks. Sometimes, these attacks are so highly focused, that they target just the key individuals with access to enterprise resources. With many attacks being too small to fall within the anti-virus and anti-malware radar, enterprises are turning to advanced IPS engines for zero-hour protection.
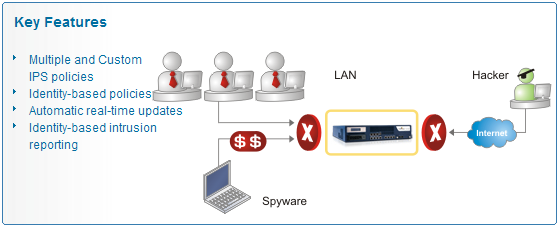
Cyberoam’s Intrusion Prevention System (IPS) solution provides powerful protection by blocking intrusion attempts, protecting against malware, Trojans, DoS attacks, malicious code transmission, backdoor activity and blended threats. It is a subscription service, offering the most comprehensive, zero-hour protection to enterprises in combination with the Cyberoam firewall, VPN (SSL VPN & IPSec), gateway anti-virus and anti-spyware, anti-spam and content & application filtering services.
Comprehensive Protection
A Cyberoam IPS support multiple protocols — HTTP, HTTPS, FTP, SMTP, POP3, IMAP, P2P and IM - and automatically detects, blocks or drops suspicious traffic. The Intrusion Prevention system delivers network-layer protection with more than 3000+ inbuilt signatures which are automatically updated.
Identity-based IPS Policies and Reporting
The Cyberoam UTM is unique in providing multiple IPS policy creation, enabling enterprises to customize policies per user or group rather than create blanket policies. In the process, it eliminates false positives that occur with blanket policies. With the multi-policy support, enterprises can define identity-based policies that restrict access depending on the users profile.
Cyberoam’s Intrusion Prevention offers user identity-based alerts and detailed reporting based on the username for both inbound and outbound traffic. Enterprises gain easy visibility into applications with user name, source, destination, period and extent of usage, enabling them to zero in on rogue users and systems easily. In addition to a dashboard report that gives an enterprise-wide overview of threat status, detailed IPS reports by Cyberoam Intrusion Prevention System giving Top alerts, Top attackers, Top victims as well as alerts with usernames and attack severity facilitate instant corrective action by enterprises in case of an intrusion.
Zero-Hour Protection
Cyberoam’s Intrusion Prevention System supports custom signatures, allowing enterprises to create their own signatures for zero-hour protection, preventing targeted attacks unique to the enterprise. The IPS signature database also includes HTTP proxy signatures that prevent masking of users surfing through an anonymous open proxy.
Centralized Security
Enterprises can centrally create custom signatures for branch offices through the Cyberoam Central Console (CCC). The IPS policies can then be centrally pushed across distributed networks, enabling enterprises to enjoy zero-hour protection at branch offices against emerging network attacks despite the lack of technical resources at these locations.